|
|
Organizations are faced with an increasingly sophisticated, constantly evolving threat landscape and limited resources to protect their environments. To keep up, many businesses count on the 24/7 hands-on expertise provided by managed detection and response (MDR) services.
SentinelOne has once again demonstrated industry-leading real world performance in the latest independent MITRE ATT&CK® Evaluation of managed security service (MSS) providers. The attack scenario in this year’s test highlights the importance of speed, visibility, and reduced noise; with SentinelOne’s Vigilance MDR+DFIR delivering:
- 100% detection of major attack steps – 14 out of 14 steps identified, investigated and reported
- Best signal-to-noise ratio amongst top performers – Providing clear and actionable analysis and not a flood of automated alerts
- Optimal Mean-Time-to-Detect and Mean-Time-to-Escalate – SentinelOne’s autonomous, AI-powered Singularity Platform balances speed and accuracy to ensure organizations stay ahead of attacks
- Enriched reporting – Our final incident report was recognized by MITRE for enrichment with contextual analysis – including a key timeline of events, a detailed technical analysis, and clear, actionable recommendations to reduce the likelihood of incident recurrence
These results clearly illustrate how SentinelOne’s Singularity Platform, combined with its Vigilance MDR + DFIR services, provide the most comprehensive, thorough, and efficient real-world protection against sophisticated attacks for every organization.

Measuring Real-World Protection | Understanding MITRE Enginuity’s ATT&CK Evals MSS Round 2
This year’s evaluation emulated the adversary behavior of menuPass (G0045) and an ALPHV/BlackCat ransomware affiliate. Prevention and remediation were not in scope of the evaluation. menuPass (aka APT10) has been active since at least 2006 and is believed to be sponsored by the Chinese Ministry of State Security. The group focuses on the exfiltration of sensitive data such as intellectual property and business intelligence in support of Chinese national security objectives. ALPHV/BlackCat, a prolific Russian-speaking RaaS group that emerged in 2021, is linked to BlackMatter, DarkSide, REvil, and other RaaS groups. ALPHV/BlackCat utilizes ransomware coded in Rust, allowing for enhanced performance, flexibility, and cross-platform capabilities.
SentinelOne Cuts Through the Noise to Deliver Expert Managed Detection & Response with Speed and Accuracy
It is estimated that security teams receive more than 1,000 events, alerts, or incidents per day, with more than half of these going uninvestigated. While visibility is critical to identifying and understanding threats, it can also lead to information paralysis and alert fatigue. As stated in the MITRE Enterprise Evaluation Round 5: “100% visibility” is not always a positive. AI and automation become critical in ensuring the right information gets to the right hands quickly and with context.
Managed Detection and Response bridges this gap by performing 24/7 detection, investigation, and mitigation of all attacker activity, summarizing incident scope, impact, and recommending critical next steps and actions to the customer.
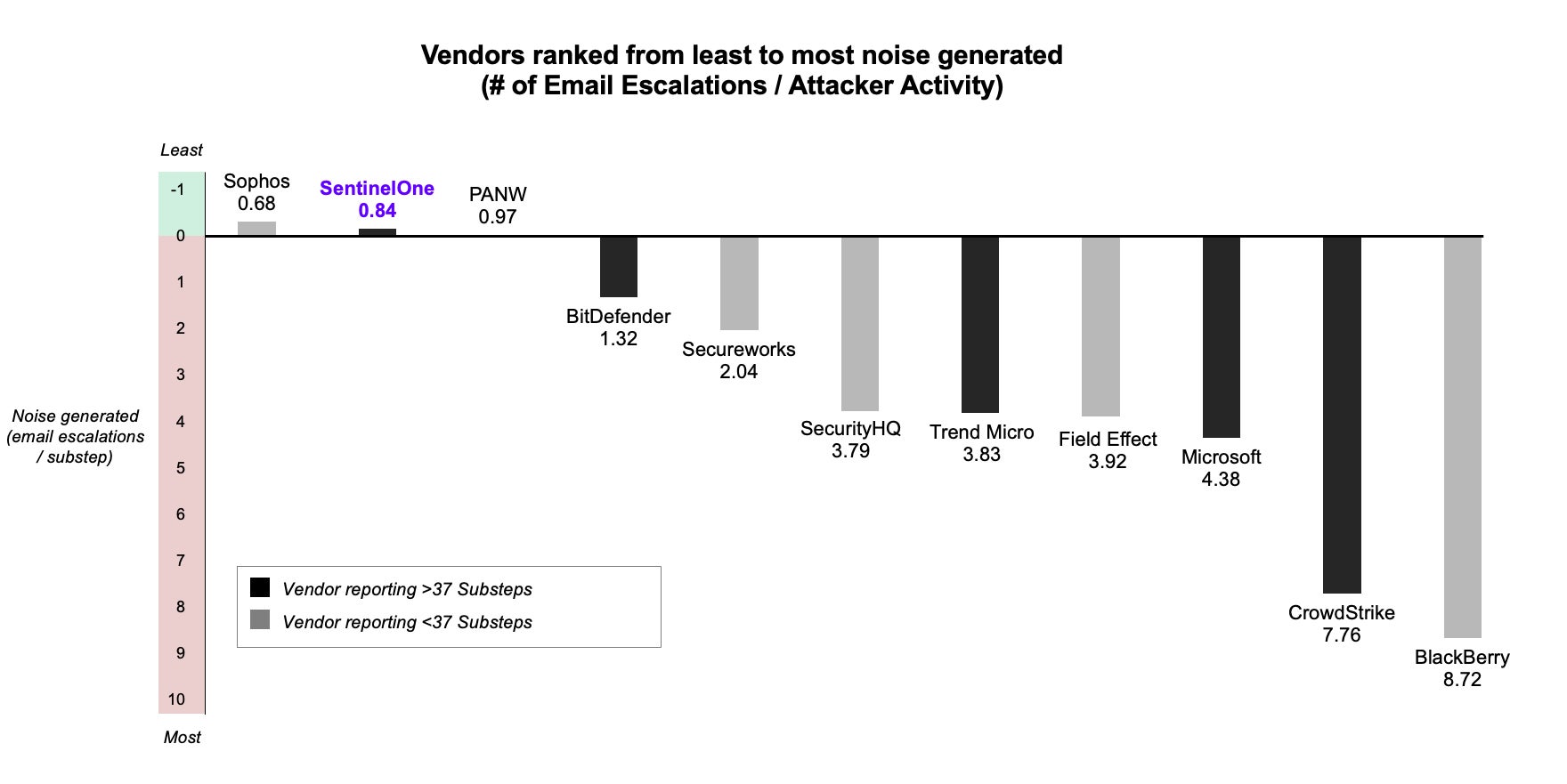
This combination of machine and human intelligence makes the Autonomous SOC a reality, mitigating and remediating at cloud scale to stay ahead of attackers while escalating only the most critical incidents for attention. This allows analysts to stay focused on what matters most. SentinelOne’s MDR team fully resolves more than 99% of all threats without requiring an escalation to the customer. As evident in the table below, many vendors bombard analysts with notifications and alerts, as many as 8 or more per unique attacker action. Security teams need to spend their time responding to critical notifications, not creating mail rules.
Mean Time To Detect | The Power of the AI-powered Singularity Platform
Not all detections are created equal. It is important to note there is a significant material difference between Mean-Time-To-Detect (MTTD) and Mean-Time-To-Escalation (MTTE), though the MITRE Evaluation does not differentiate between the two. MITRE defines MTTD as the time each vendor took to notify the customer about every stage of the attack. Conversely, SentinelOne defines MTTD as the time when technology first notifies a human analyst about suspicious or malicious activity.
The Singularity Platform detects and blocks threats in near real-time; often sub-second or within seconds. During the MITRE evaluation, components of the platform were turned off to allow the MITRE test to run. While MITRE did not evaluate participants based on our definition of MTTD, our assessment showed that our MDR analysts were notified within 3.3 minutes on average of every major attack step that was detected.
Only the most critical alerts, or those requiring human intervention or approval, are escalated after careful investigation. The time between the detection of the activity (first alert) and the escalation to the customer is known as MTTE.
Mean Time To Escalate | Balancing Accuracy & Speed
Once alerted by The Platform, our MDR analysts conduct their expert analysis, filtering out unrelated activity, correlating multiple data points, and in cases of actual incidents, performing containment and mitigation actions – all before escalating to the customer. During the evaluation, SentinelOne’s MDR experts achieved an incredible 47 minutes between detection and escalation to the customer — reported by MITRE as MTTD, but often referred to as Mean-Time-To-Escalate (MTTE) —ensuring that within 50 minutes of each major stage of the attack, the customer was presented with a single clear summary of the activity identified and the response actions that either should be or have already been taken on their behalf.
This final escalation to the customer is the last stage in the response process – not the first. Extremely low MTTD results (especially when combined with a low signal to noise ratio) should be a red flag for customers seeking MDR services. Short time frames imply a lack of expert analysis, investigation and response; meanwhile, rapid auto-notifications at high volume only creates additional noise for customers to sort through.
SentinelOne provides our customers with both exceptional Mean-Time-to-Detect (MTTD) on the Singularity Platform and Mean-Time-to-Escalate (MTTE) from our MDR team.
In Real-World Scenarios, Noise to Signal Matters
MDR services are trusted partners for security teams and their real value lies in turning signal noise into actionable insights. SentinelOne’s MDR+DFIR teams:
- Triage and investigate all suspicious activity on behalf of customers;
- Filter out false positives;
- Investigate the scope and impact of malicious activity;
- Escalate only the incidents that matter most for the customer’s business (see figure 1); and
- Provide clear, actionable updates until the incident is contained and remediated (see figure 2 for example notification).
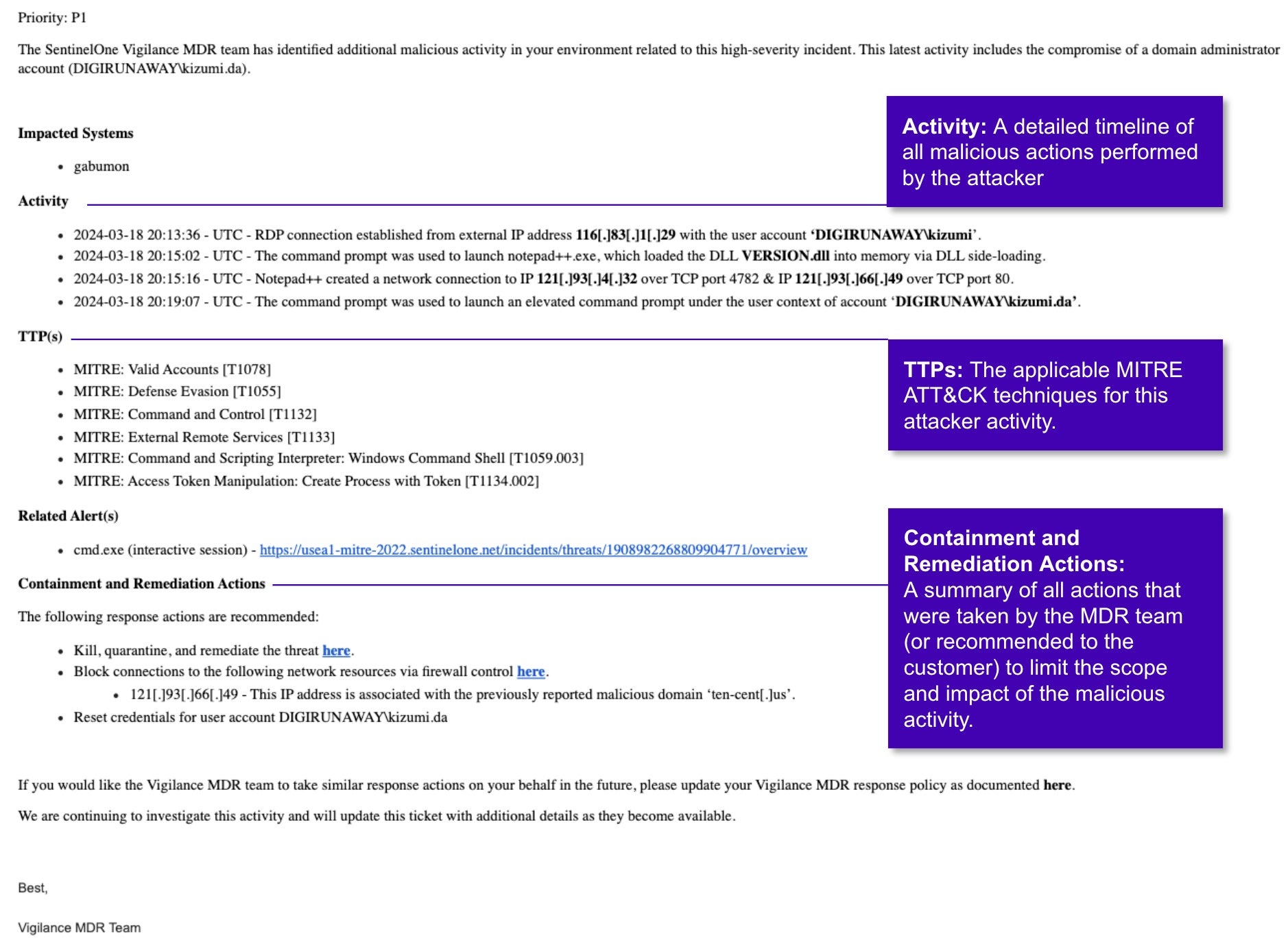
SentinelOne’s performance in this evaluation shows that our team of analysts and threat hunters identified and investigated all major steps of the attack, filtering out unrelated alerts and unnecessary details, and providing our customer with detailed, actionable updates and guidance.
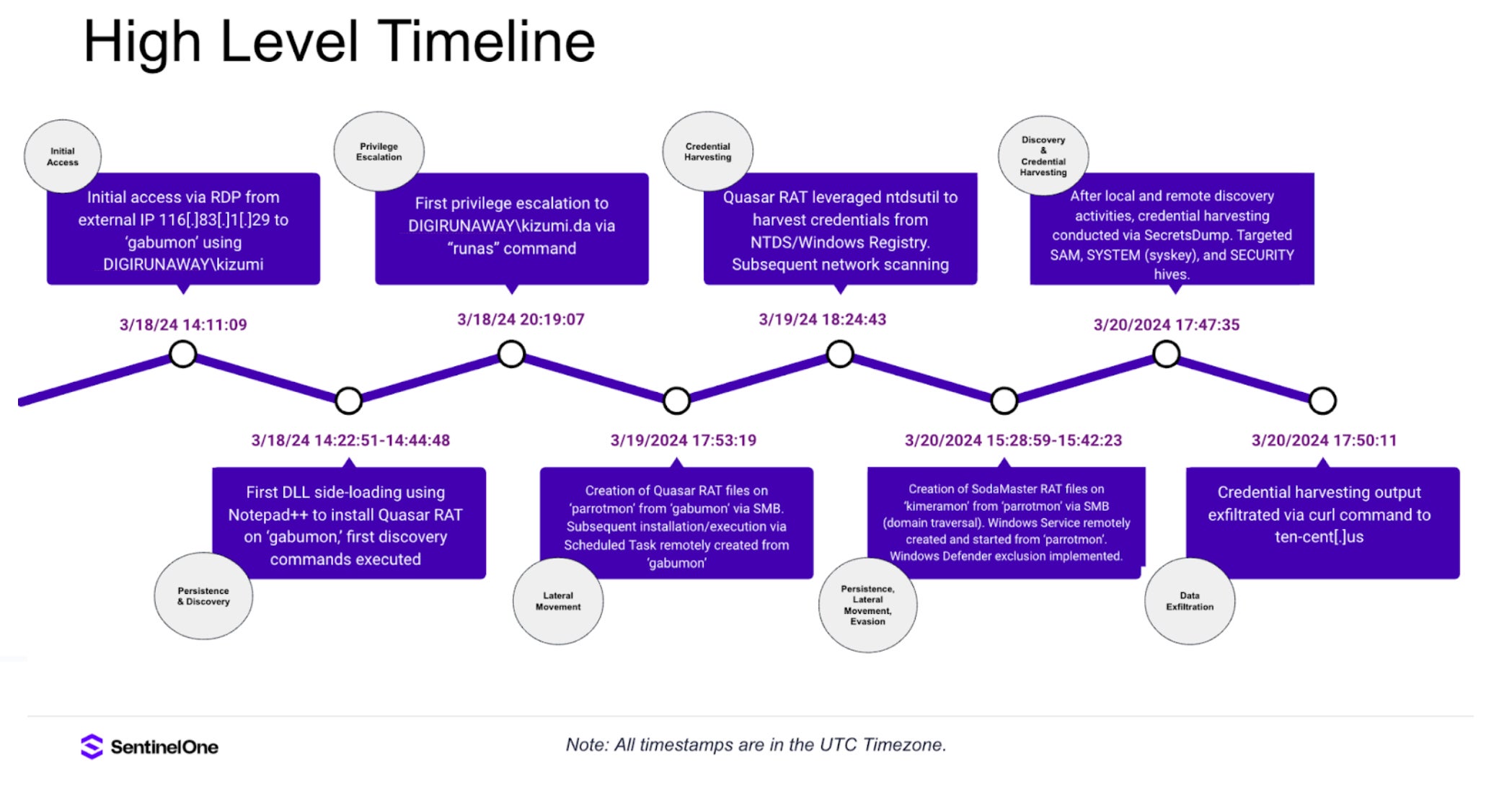
At the conclusion of the incident, our team delivered a detailed and comprehensive incident report, including a full view of the scope and impact of the attack (figure 3) and detailed technical analysis (figure 4).
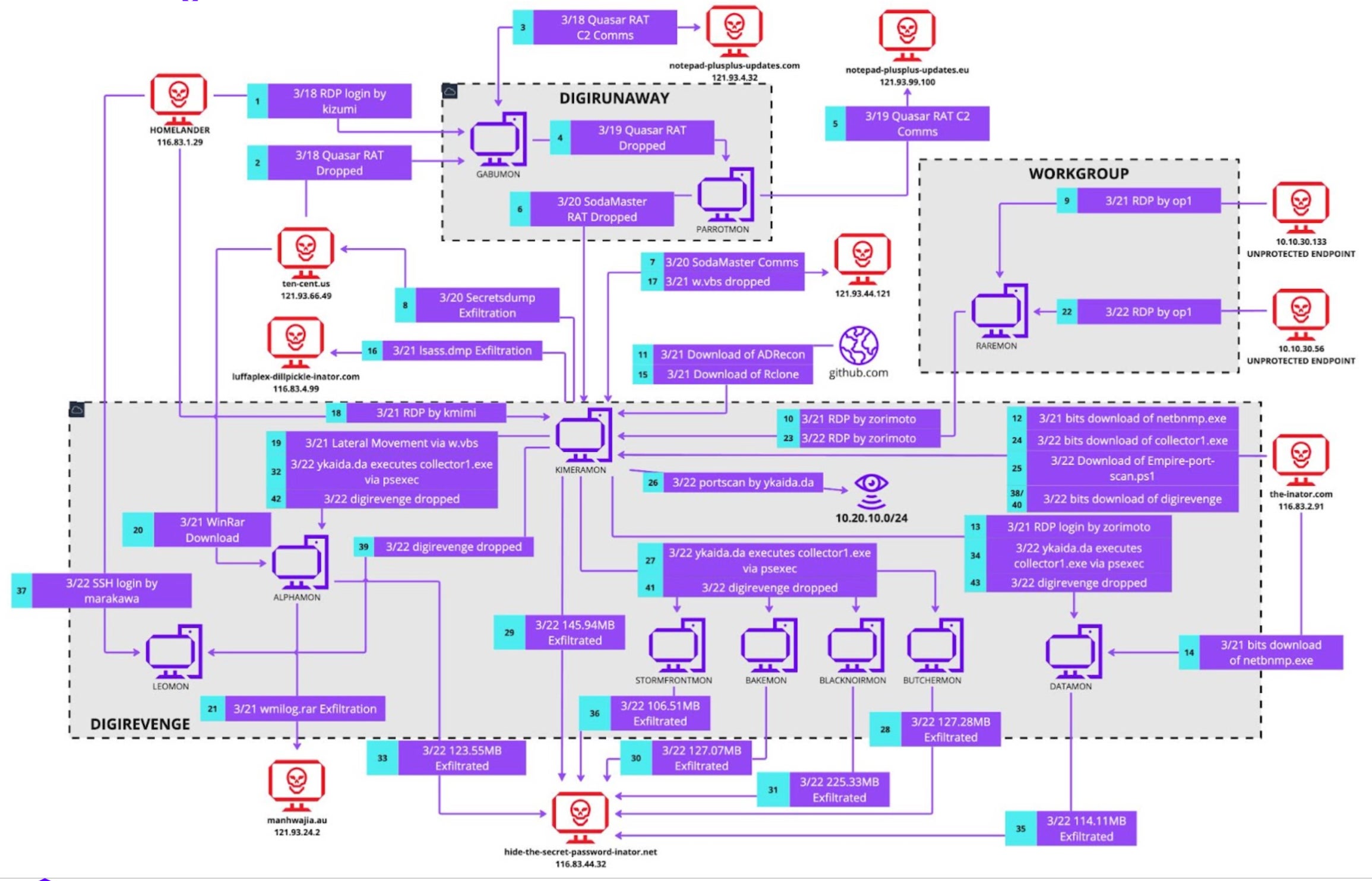
A Team of Skilled Experts Augmented by Powerful Technology
At SentinelOne, we prioritize real-world protection for our customers, combining our autonomous, AI-powered Singularity Platform with a global team of MDR analysts, investigators, and threat hunters to cut through the noise and take proactive mitigation actions to prevent attacks. Together, our machine and human intelligence enable us to continue our leading performance in ATT&CK Evaluations based on real-world protection and results. This latest evaluation proves how we deliver on what customers need in an MDR provider and why leading partners and organizations of all sizes choose the Singularity Platform to autonomously detect and prevent threats and achieve complete enterprise protection.
We encourage buyers to continue to lean on third-party evaluations such as MITRE Engenuity to assess the best fit for their organizations. Dive deeper into SentinelOne’s leading performance over five years of MITRE Engenuity ATT&CK evaluations here. To join the ranks of other customers who have gained peace of mind and simplified their security with SentinelOne’s MDR services, learn more about Vigilance Respond Pro.



